
36% of MSPs Are Struggling to Acquire New Clients – Here’s the Secret to Standing Out
As trusted strategic partners, businesses increasingly rely on managed service providers (MSPs) to protect their IT environments. If you’re an MSP offering cybersecurity services, you likely already know it’s one of the most lucrative services in your portfolio.
That being said, every MSP knows this, so the market is becoming highly competitive. If you’ve been operating in this space for some time, you may have noticed a slow but gradual deceleration in your business’s growth. You’re not the only one experiencing this.
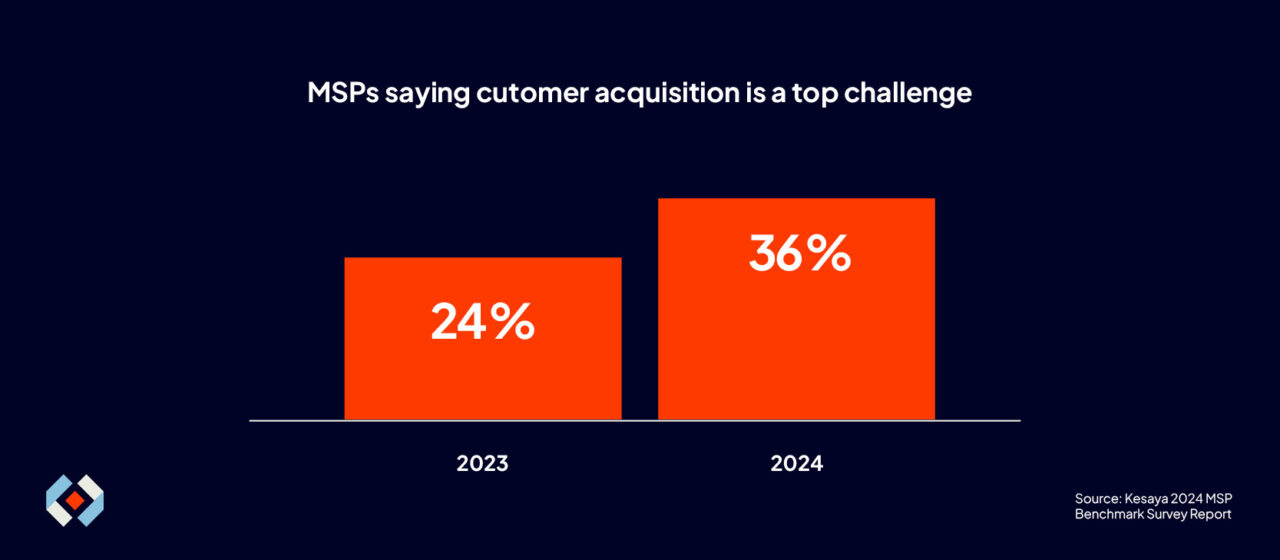
Most MSPs surveyed for the Kesaya 2024 MSP Benchmark Survey Report identified “acquiring more customers” as their number one challenge. More importantly, the percentage of respondents who identified customer acquisition as a top challenge grew from 24% in 2023 to 36% in 2024.
The MSP landscape is indeed getting crowded. But that doesn’t mean there are no more opportunities for growth. However, for your MSP business to continue growing, you need to stand out from the competition.
While there is no silver bullet to achieve this, security solutions that deliver real-time network visibility can give you a significant advantage. Here are 10 reasons why.
1. Boosts Proactive Threat Detection
Reactive measures cost more than time.
Cyber attack events, such as command-and-control (C2) beaconing, lateral movement, and privilege escalation attempts, can generate anomalous network traffic. However, they can occur any time.
If you’re not monitoring the network while these events are happening, you won’t be able to detect the anomalies they generate. When you have real-time network visibility, you can capture anomalous traffic behaviors in your clients’ networks as they occur.
Unlike sampling-based approaches, real-time network monitoring enables proactive threat detection. You gain insights into suspicious behavior before an attacker can cause costly damage, which leads to another benefit.
Let’s discuss that next.
2. Improves Incident Response
Clients are happier if you can stop a cyber attack from causing any damage.
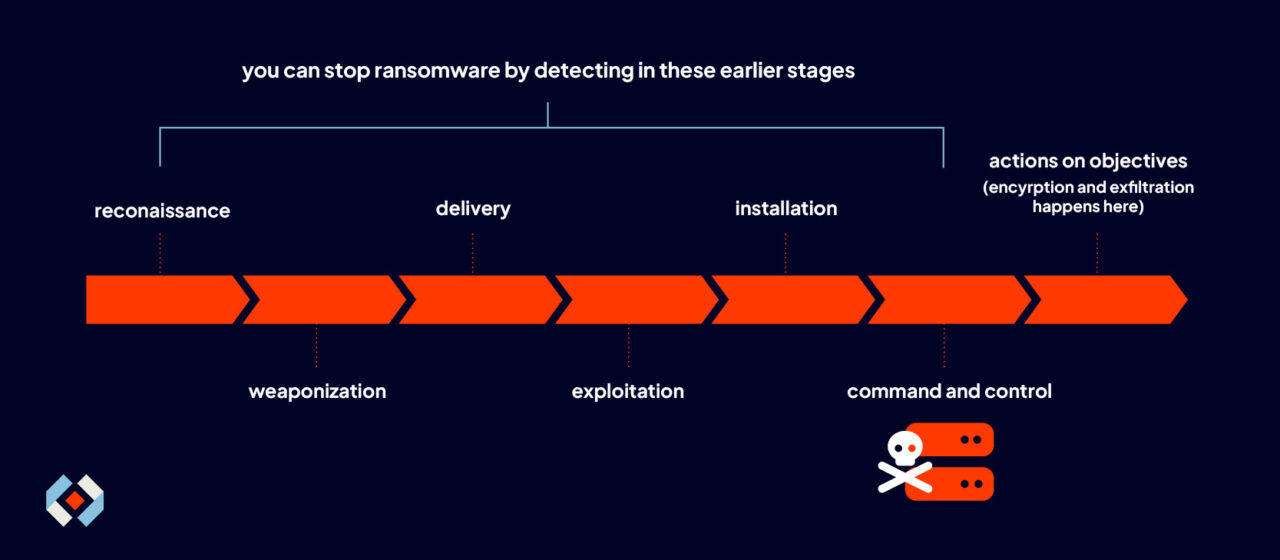
The earlier in the cyber kill chain you can detect an attack, the better your chances of stopping it. Let’s say some ransomware has infected one of your clients’ systems. This ransomware happens to be one of the newer types that performs double extortion.
Meaning, it encrypts and exfiltrates files, and demands payment for both.
Since this ransomware needs to exfiltrate stolen files to a command-and-control server (C2), it has to communicate with that server in the early stages of the attack.
Thus, if you can detect that communication process, you can contain and eradicate the malware before it can start encrypting and exfiltrating files.
3. Mitigates Data Breach Risk
Protect clients from a multi-million dollar fallout.
The global average cost of a data breach is now USD 4.88 million. This amount usually comes from the cost of operational downtime, loss of customers, regulatory fines, legal expenditures, and many others. Your clients would undoubtedly want to avoid these expenses.
Most breaches involve data exfiltration. As hinted in the previous section, exfiltration processes don’t happen arbitrarily. Adversaries typically conduct exfiltration in the later stages of an attack.
So, if you can detect early signs or indicators of compromise (IOCs) related to that attack, you can prevent the data breach from happening. You can only achieve that through real-time network visibility.
4. Optimizes Client Reporting
Show clients the current state of their network, not snapshots from hours or days ago.
Many MSPs submit reports containing outdated data. That’s the best you can do if you rely on sampling-based monitoring solutions. You can provide a more accurate and up-to-date snapshot of your client’s network if you monitor it in real-time.
Real-time monitoring can deliver actionable AND timely information for several security-related reports, including:
- Security posture reports
- Threat intelligence reports
- Security incident reports
- Vulnerability assessment reports
- And others
5. Enhances Regulatory Compliance and Audit Readiness
Help your clients exceed compliance obligations.
Some of your clients may be subject to regulatory compliance mandates like the Health Insurance Portability and Accountability Act (HIPAA), the Payment Card Industry Data Security Standard (PCI DSS), and the General Data Protection Regulation (GDPR).
Many regulatory requirements explicitly or implicitly call for real-time monitoring. For example, PCI DSS 4.0.1 Requirement 5.2 guidance recommends “active, real-time” scanning to improve malware detection.
As discussed earlier, real-time monitoring is more effective at catching threats than periodic scans. If regulatory mandates only require periodic scans, you can help your customers exceed that baseline requirement and increase their chances of achieving compliance if you implement real-time monitoring.
6. Streamlines Service Level Agreement (SLA) Management
Meet SLA requirements with ease by significantly reducing the risk of downtime.
Disruptive cyber attacks like malware outbreaks, Distributed Denial of Service (DDoS), and ransomware infections pose a serious risk to your SLA uptime guarantees.
To avoid SLA violations, you must nip these threats in the bud before they cause an outage. By implementing solutions that enable real-time network visibility, you’ll be more capable of detecting and remediating disruptive threats before they escalate.
7. Optimizes Resource Allocation and Cost-Savings
Put people, tools, and attention in the right place, at the right time.
Real-time insights enable you to see which clients, systems, or potential threats need your immediate attention at any given time. This level of visibility allows you to prioritize and resolve issues faster, preventing them from piling up and overwhelming your team.
As a result, you’ll deploy staff, tools, and other resources more efficiently, and even uncover cost-saving opportunities.
8. Enables Scalable Multi-Client Management
Deliver quality managed services at scale.
Managing and securing multiple customers is no easy task. Security issues often seem to pop up all at once—but do they really? Or is that just how it feels when you’re working with delayed or incomplete information?
This false perception makes it difficult to accommodate more clients and hinders business growth.
As noted in the previous section, real-time visibility lets you address security issues across multiple clients more efficiently. Therefore, you can expand your MSP business without adding unnecessary complexity.
9. Drives Customer Satisfaction and Retention
Give customers more reasons to stay.
In our introduction, we highlighted the difficulty MSPs face in acquiring new customers. Since acquisition has become increasingly challenging, you can’t afford to lose customers. You should put more effort into retaining the ones you already have. Real-time network visibility plays a vital role in that endeavor.
As explained throughout this article, real-time network visibility unlocks several benefits that can revolutionize your MSP business. All these benefits combined result in greater customer satisfaction. As long as you keep your customers happy, they’ll have fewer reasons to leave and more reasons to stay.
10. Future-proofs Your Security Offering
Stay ahead of threats and your competitors.
Cyber threats aren’t just increasing. They’re also evolving. New ransomware variants are encrypting files faster. A proof-of-concept polymorphic keylogger could use ChatGPT to generate its polymorphic property. And so on.
Despite the new functionality that cybercriminals are incorporating into bleeding-edge malware, one characteristic remains: almost all these threats still use some form of network communication.
Until that characteristic becomes obsolete, security solutions with real-time monitoring will keep you and your clients abreast, if not one step ahead, of adversaries.
Resources that might interest you.

Indicators of Compromise: What They Are and How to Identify Them
Cybersecurity is essential, but managing it has never been straightforward. The more tools you add, the more vulnerabilities you introduce….

